SASE and ZTNA: Empowering and Protecting Hybrid Workforces

The widespread adoption of hybrid and remote work is changing the way enterprise organizations access and store data. In fact, U.S. organizations surveyed post-pandemic stated that nearly half (48%) of their employee base will continue to work from home at least part of the time.1
As a result, companies are looking for new networking and security solutions that can protect their devices, data, apps and corporate information assets against cyberthreats without compromising network performance.
So, what’s the solution?
The answer lies in identity-driven security. Individualized access to corporate systems and devices has emerged as today’s solution to effectively protect your data, mitigate risk and ensure compliance with regulatory requirements.
Work from the office, at home or hybrid?
In the post-pandemic age, the question driving uncertainty and hesitation across organizations is, “Should we adopt an at-the-office, remote or hybrid work model?” The reality is that we live in unpredictable times—so why not all three?
COVID, the economy, the rise of automation and the progression of artificial intelligence are transforming the nature of work. By considering all three work models, enterprises can remain flexible during uncertain times, find the best solutions for their specific needs and stay competitive in an ever-changing business environment.
Additionally, being open to different work models offers numerous internal benefits for companies. Remote work allows for a larger pool of talent to be considered, as geographical location is no longer a barrier. This can also result in cost savings for both the employer and employee, as expenses such as commuting and office space are reduced.
The hybrid work model offers the best of both worlds, enabling employees to enjoy the flexibility of remote work while still having access to the resources and collaboration opportunities of a physical office. Hybrid work also allows for increased work-life balance and flexibility, which leads to a more satisfied and productive workforce.
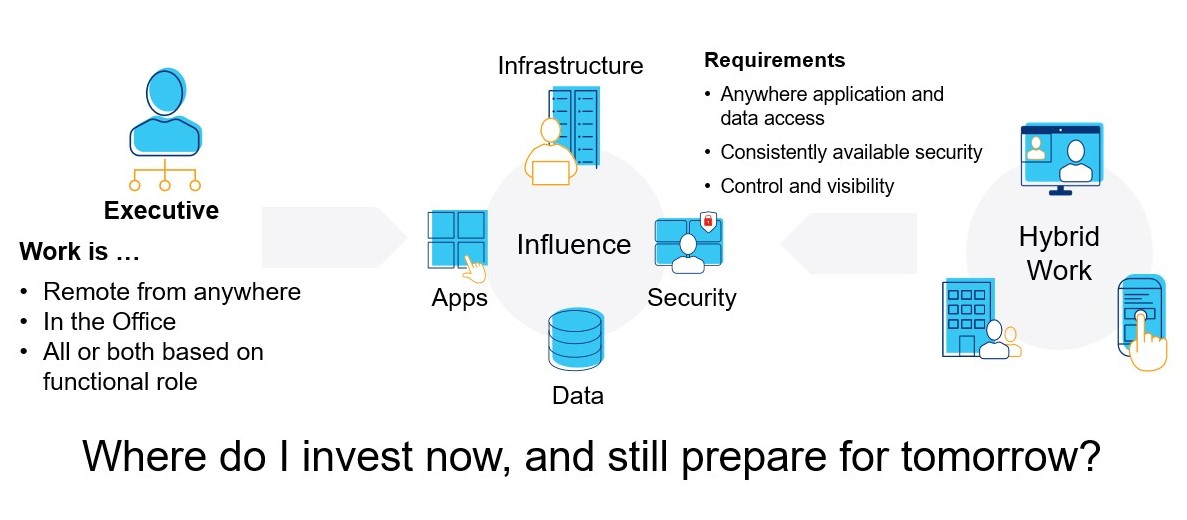
Figure 1: Reference diagram for hybrid work
Security risks of VPN access in a hybrid business environment
While the benefits of adopting hybrid or remote work may far outweigh the drawbacks, both models come with a host of security risks.
During the pandemic, when organizations rapidly shifted to hybrid or remote work, VPN solutions provided authenticated access to the corporate data center to give employees an in-office experience. While the approach worked, it was a stop-gap measure that yielded less than ideal situations.
Employees authenticated access to the entire corporate network rather than to specific information they had permissions to use, creating an attack vector vulnerability. Ransomware attacks increased by nearly 500%, making their way into the corporate data center from the employee device through the VPN.2
With employees now accessing company networks and data from home or on the go, and with user devices being vulnerable to cyberattacks when used outside of the secure corporate network, placing identity at the center of your security strategy is paramount. By making identity the new security perimeter, companies can control access to their sensitive data and applications much more effectively.
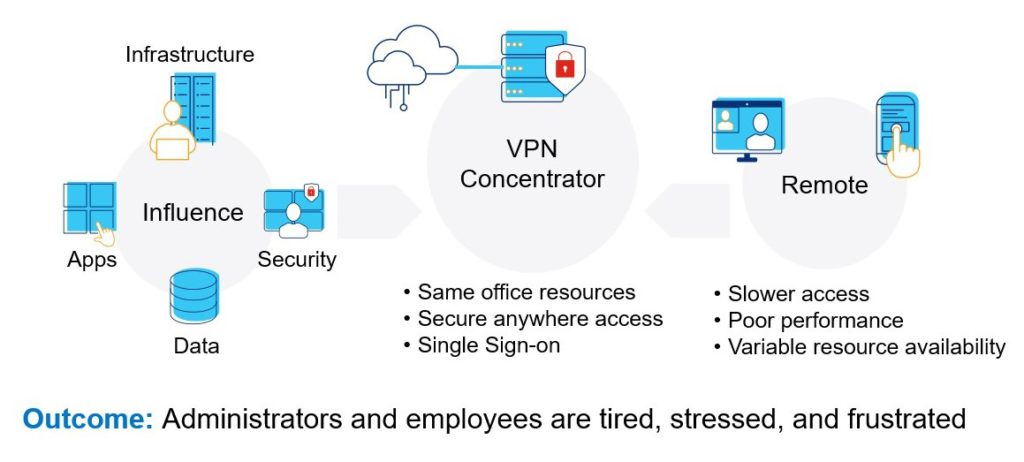
Figure 2: Reference diagram for drawbacks of VPN concentrators providing authenticated access
Identity-driven security for hybrid workforces
Secure Access Service Edge (SASE) and Zero Trust Network Access (ZTNA) offer many advantages to enterprise organizations who want to secure their IT resources and support dynamic, distributed, anywhere-anytime access to those resources.
What is SASE?
SASE is a networking and security architecture that provides high-performing, secure and seamless access to resources, regardless of location or device, through a combination of optimized network connectivity, such as software-defined WAN, and cloud-based security functions.
One of the primary ways that SASE improves both networking and security is by integrating security functions, such as VPN and firewall, with cloud security services into a single solution delivered as a cloud service. This eliminates the need for multiple hops between different security solutions, which reduces latency and boosts the overall performance of the network.
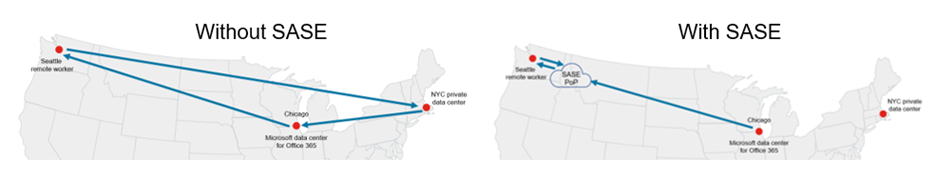
Figure 3: Reference diagrams for networking with and without SASE
What is ZTNA?
As enterprise perimeters continue to evolve, and security risks can now originate from both inside and outside the network, ZTNA is a security model that assumes all network traffic is potentially malicious and restricts access to resources based on user identity, device health and context.
ZTNA (as part of SASE) helps provide individualized, identity-driven security for hybrid employees, no matter where they happen to be working, and here’s how:
- Risk awareness: Continuous monitoring and evaluation of the security posture of devices, networks and users. The system analyzes various contextual information, such as device health, location, time, user identity and behavior to determine if an access request poses a risk to the organization’s security.
- Least privileged access: Access to resources and systems is granted only on a “need to know” basis, rather than granting unlimited access to all users and devices. Users are given only the minimum level of access necessary to perform their job functions.
- Continuous access verification: Monitoring and verification of access requests to resources and systems occurs on an ongoing basis. Instead of access being granted based on network location or device ownership, it is granted (or denied) each time a user attempts to access a resource, based on information like user identity, device health and other contextual information. Credentials aren’t just checked at the network’s perimeter and then ignored; they are monitored on a continuous basis so that security teams can spot and mitigate anomalous activity.
SASE + ZTNA: Better together.
When SASE and ZTNA are integrated, they provide a powerful solution for granular access control to applications and data.
SASE provides a single platform for managing all access requests, regardless of where they come from, and provides secure access to applications and data across all network edges.
ZTNA enforces a zero-trust approach to security, meaning that all access requests are treated as untrusted and must be authenticated and authorized before access is granted.
SASE and ZTNA enable IT teams to deploy a seamless, comprehensive approach to security that minimizes risk, ensures compliance and simplifies management. This means that users can securely access the applications and data they need, from anywhere, at any time, without worrying about security risks.
By integrating SASE and ZTNA, enterprise organizations can benefit from:
- Managed detection and response
- Managed endpoint detection and response
- Incident response
- Threat intelligence
- Virtual SOC
- Managed SIEM
- Vulnerability assessment
These advantages are becoming increasingly important as organizations move toward a cloud-based, perimeter-less infrastructure that supports hybrid work models, where defense against increasingly sophisticated cyberattacks is crucial.
Unify (and simplify) your networking and security
Lumen® SASE Solutions plus ZTNA support hybrid enterprises with a single, cloud-delivered service that integrates networking and security for better management and control. Combined with the power of the Lumen network, SASE solutions optimize enterprise organizations for a distributed, cloud-first business environment by enabling them to unify disparate security policies, move security functions closer to PoP/Edge locations, lower latency and improve application performance.
Lumen helps enterprise organizations successfully navigate the challenges of the work-from-anywhere era by delivering on three key requirements:
- Maintaining productivity on any device, from virtually any location by providing the most direct route from the end-user to the applications and data they need.
- Simultaneously filtering and securing that access based on user credentials, application and data content, device used and network configuration.
- Achieving the visibility, control and flexibility to detect and respond to threats, and applying authorized access while placing limits on asset availability on a per use basis.
Partner with Lumen to successfully implement these crucial IT factors and experience a smooth transition to a hybrid work model for maximum ROI.
Sign up for our SASE Assessment to find out where you stand in your journey and receive a tailored adoption roadmap to match your business needs.
1Versa Networks and Sapio Research, Global Digital Transformation Survey: Experiences and Attitudes Towards a Post-COVID Workforce, 2021.
2Infosecurity Magazine, Ransomware Attacks Grew by 485% in 2020, 2021
AUTHORS
Darren Wolner
Darren leads Lumen’s SASE, SD-WAN and Edge Gateway product portfolios. This includes setting vision, goals and agile initiatives that drive the product roadmap, enabling Lumen to innovate and align with market trends to meet the demands of our customers in the Enterprise, Mid-Market and Public Sectors. In this role, Darren leads a product team focused on delivering Software Defined Networking and cloud-based security solutions, including SD-WAN, Secure Web Gateway (SWG), Firewall-as-a-Service (FWaaS), Zero Trust Network Access (ZTNA), and Cloud Access Security Broker (CASB). He and his team enjoy helping our customers navigate their business transformation journey with fully managed, all-digital, on-demand experiences while helping them protect their environments from the largest and most recent cyber threats.
Mike Robles
A Senior Director of Product Management at Lumen Technologies, Mike has been involved with networking and communications product management, design and development for over 17 years. He has been with Lumen since 2010 via the Level 3 acquisition.
This content is provided for informational purposes only and may require additional research and substantiation by the end user. In addition, the information is provided “as is” without any warranty or condition of any kind, either express or implied. Use of this information is at the end user’s own risk. Lumen does not warrant that the information will meet the end user’s requirements or that the implementation or usage of this information will result in the desired outcome of the end user. This document represents Lumen’s products and offerings as of the date of issue. Services not available everywhere. Business customers only. Lumen may change or cancel products and services or substitute similar products and services at its sole discretion without notice. ©2023 Lumen Technologies. All Rights Reserved.





