Swipe At Your Own Risk: What you need to know to combat Point of Sale malware PoSeidon

If you use a credit card to make purchases at your local retailer, gas station, restaurant or bar, it can be compromised – if it isn’t already. Black market demand for user and credit card data has made Point of Sale (PoS) system compromise a lucrative business, leaving breached retailers to fight a war of both reputation and liability. As PoS systems are targeted with greater frequency, new families of malware are developed and extended at a breakneck pace. Over the past several years, we have seen successful high profile compromises resulting from lax security policies and procedures to very sophisticated targeted attacks on major retailers. And now, with PoS malware continuously evolving and becoming more difficult to detect, the security community, as well as retailers, has a real challenge on its hands.
As part of the work we do to protect our network and customers, Level 3 Threat Research Labs recently completed a study and set of recommendations on a sophisticated strain of PoS malware known as PoSeidon.
Background on PoSeidon
On March 19, Palo Alto Networks’ Unit 42 released their findings on a new Point of Sale malware family dubbed FindPOS. On March 20, Cisco’s Talos Group released their findings on the same family – now dubbed PoSeidon. Both groups published the pre-defined command-and-control (C2) and exfiltration server domain lists found in the code, which we were able to leverage in our investigation. Most recently, Damballa reported on new malware versions containing new C2 lists.
This new malware family scrapes the credit card data found on compromised Microsoft Windows PoS systems, installs a key logger, and then transmits captured data to exfiltration servers. This means as soon as you swipe your card the hackers soon may have access to the data if that PoS terminal or system has been breached.
Shortly after identification of the malware, and as media coverage expanded, the Level 3 Threat Research Labs began tracking network traffic for the IP addresses associated with the malware domains.
What Level 3 Threat Research Labs Found When Tracking PoSeidon
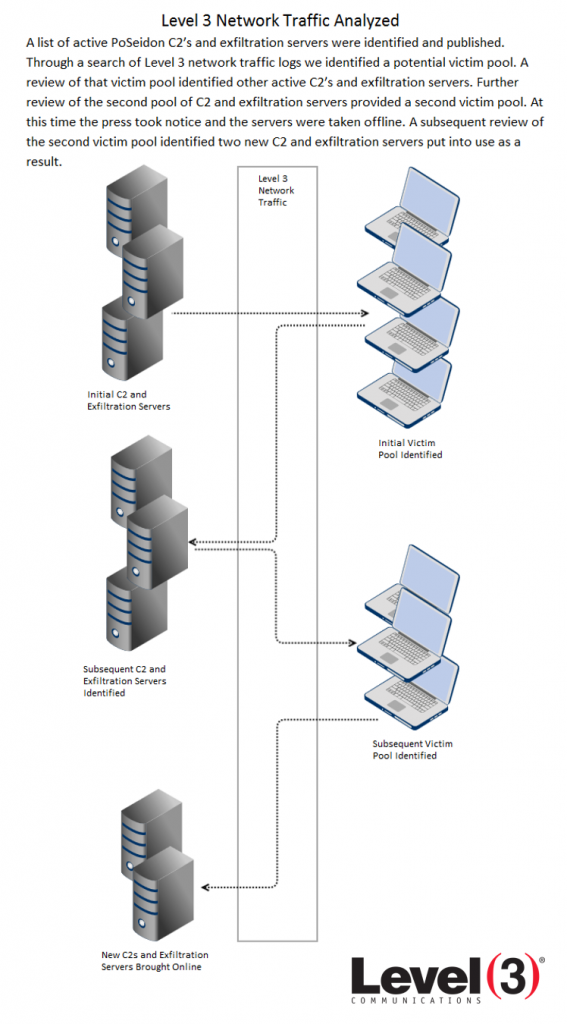
For this analysis, the initial step was determining the victims communicating with the original set of C2s and exfiltration servers initially identified. Those hosts’ top communication peers led to the second set of C2s and exfiltration servers, their victims, and then a final set of C2s and exfiltration servers. This cyclical investigative process terminated when the last set of top communication peers led to no new C2s and exfiltration servers. A list of all C2 and exfiltration domains is included later in the post.
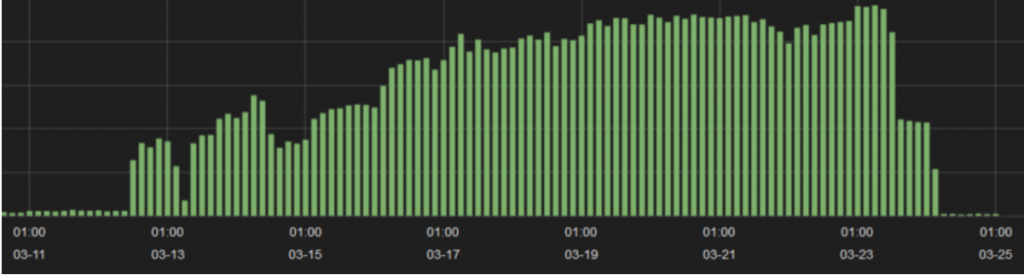
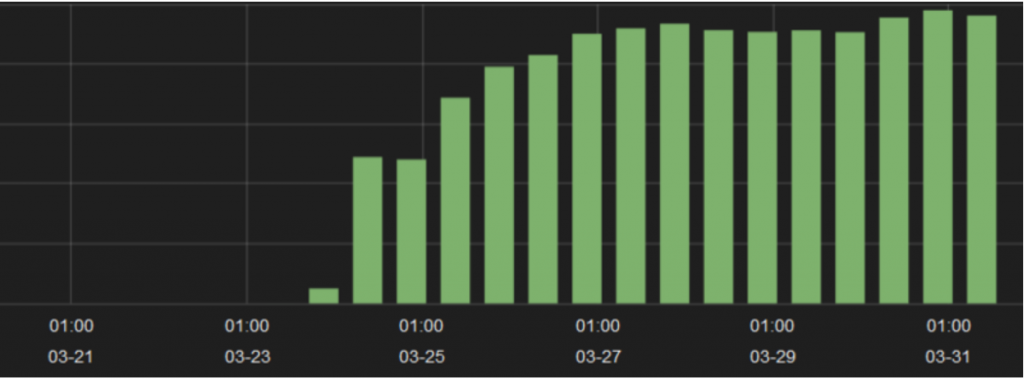
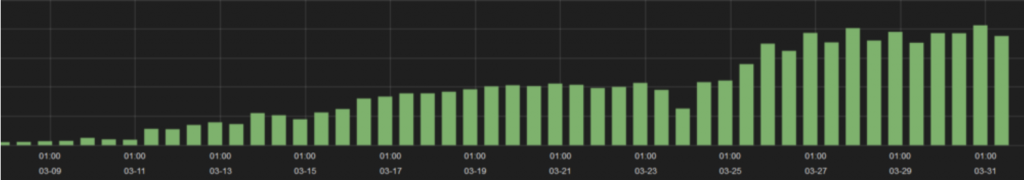
Although the initial papers regarding this malware were released on March 19 and 20, this research did not gain significant media attention until March 23. Within 24 hours, the traffic to the previously identified hosts all but dried up. A small volume of traffic to juindorey[.]com remained, but we noted that this host (46.30.41.159 at the time) was on a network not used with the others so it may have been considered a lower priority for takedown or reporting from abuse incident handlers across the globe.
We were able to determine the identities of the C2 (89.144.2.148) and exfiltration hosts (46.161.40.104, 146.185.150.48) that were brought online once the others were publicized and discarded, or taken down by the network owners.
We then verified that changes to the domain DNS records had taken place – confirming what we found. The bad actors established new DNS A records for at least two of the domains on March 25, which allowed the compromised hosts to resolve a few of the hard-coded domains in their system for continued data exfiltration.
Below is a full picture of the overall traffic linked to PoSeidon. The traffic for initial C2s and exfiltration servers up to March 24 was small relative to the traffic after the initial set of servers were taken offline. The first half was comprised of 6 C2s and 7 exfiltration servers – conversely the post March 24 traffic is predominantly two C2s and two exfiltration servers. This could be due to the fact they simply couldn’t obtain as many systems as they had previously due to the awareness drawn by press coverage or they panicked.
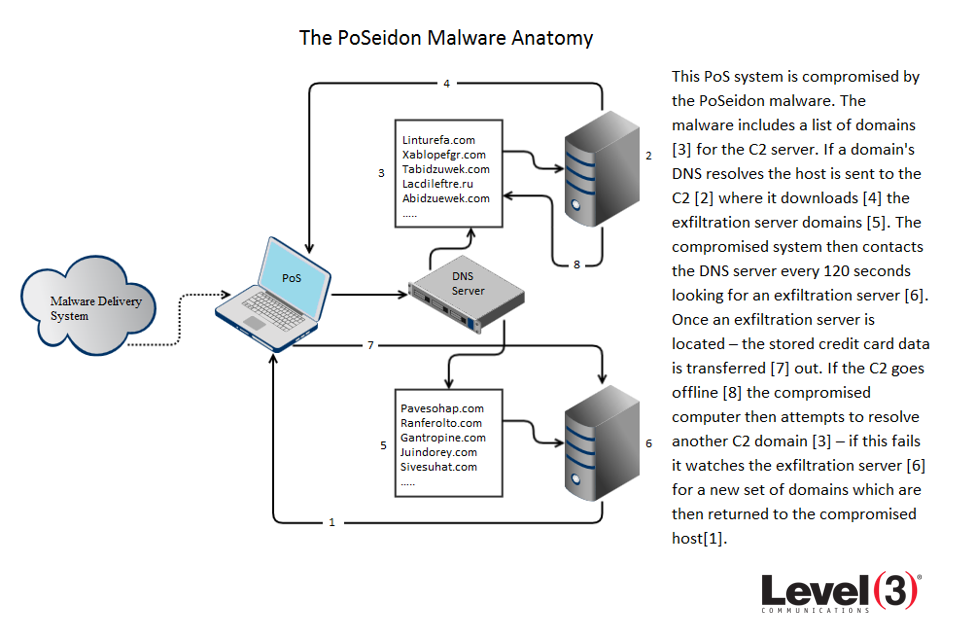
How PoSeidon Works
Upon execution, this malware starts a process called Loader. The first thing Loader does is to determine its method of persistence. It either replaces existing Windows services or installs itself as a new one, depending on the system’s configuration. After this is complete, the malware resolves a list of pre-defined C2 domains for the host to contact.
It is common for malware authors to insert lists of domains into the malware and then activate the domains and publish the DNS “A” records as needed. This allows them to continually assign the domains to different networks as needed to avoid detection or blocking. If the authors inserted IP addresses into the malware code, it would be easier for the traffic to be blocked on the Internet. In this case the operators of the botnet are continually taking domains offline and bringing others online as needed.
Recently, the Threat Research team observed the following C2 domains and their associated IPs if they were active at some point:
lacdileftre.ru
linturefa.com – resolved to 91.220.131.116
mifastubiv.ru – currently has address 89.144.2.148
tabidzuwek.com – resolved to 31.184.192.196
tabidzuwek.ru
weksrubaz.ru – currently has address 89.144.2.148
xablopefgr.com – resolved to 91.220.131.116 then 93.171.202.168
xablopefgr.ru – resolved to 91.220.131.87
litramoloka.com
litramoloka.ru
molokalitra.ru
apporistale.com – currently has address 46.161.40.106
cawasuse.ru – currently has address 89.144.2.152
dinghareun.ru
dingdownmahedt.ru
ferepritdi.ru
terethaundv.ru
howthatficy.ru – currently has address 146.120.110.104
lasttrainforest.com
refherssuce.ru
rabbutdownlitt.ru
reswahatce.ru
srachechno.com – currently has address 89.144.2.148
servelatmiru.com – currently has address 46.161.40.109
mehanistran.com – currently has address 216.246.98.85
switlawert.com
vesnarusural.ru
petronasconn.ru
restavratormira.ru
serppoglandam.ru
wertstumbahn.ru
queryforworld.com
serfilefnom.ru
Once a TCP connection is established with a C2 on port 443, the compromised host downloads a new binary named FindPOS that installs and executes a new process on the host. Amongst other actions, FindPOS scans the host’s storage devices for numeric strings that indicate credit/debit card data. These strings start with the numbers 4,5, or 6 and are 16 characters long (for Visa, MasterCard and Discover cards) or are strings that start with the number 3 and are 15 digits long (for American Express cards). FindPOS then uses the Luhn Algorithm to perform card number verification on qualifying strings, bundling and storing valid card numbers for future exfiltration. Now that it has all existing stored data, the malware logs subsequent keystrokes, so that it can capture more detailed data that might include PIN numbers or other personally identifiable information.
Each FindPOS binary includes a series of hard coded exfiltration server domains as well. The compromised host is instructed to compile the credit card data and forward it to the exfiltration site with an ‘HTTP POST’. The hosts are instructed to attempt contact with an exfiltration server every 120 seconds. If the connection is established then the data is exfiltrated, along with logs indicating whether the data files have been discovered prior to exfiltration. This allows the herders to release from the botnet, minimizing their chance of discovery or data sabotage.
We noted the IP addresses if active:
andbohemut.com
bejustoftun.com
berigusaf.ru
betroninsi.com
dilelanang.ru
forttapaha.ru
ftjuunbesto.ru
gantropine.com – resolved to 151.236.11.167 – currently has address 93.171.202.168
gutontredsup.com – currently has address 46.161.40.103
hepretfortna.ru
juindorey.com – currently has address 46.30.41.159
latemiishe.ru
leladingna.com
letgrownast.com
masquarten.com
nawertoby.com
pavesohap.com – resolved to 185.13.32.76 – currently has address 46.161.40.102
polutenign.ru
pomdonekw.ru
qwertygontul.com – resolved to 185.13.32.95 – currently has address 46.161.40.104
rechedtthaten.ru
renferolto.com – resolved to 185.13.32.118
repherfeted.com – currently has address 89.144.2.150
righletfoligh.ru – resolved to 194.58.107.31 – currently has address 146.185.150.148
saqunold.ru
sedsoceheg.ru – resolved to 194.58.107.31
silawecxla.ru
sivesuhat.ru – resolved to 91.220.131.108
stenfirthsta.com
wekustines.ru
windetrusty.com
Interestingly, FindPOS also has the ability to download and execute other malware. After the HTTP POST takes place – if the exfiltration server responds back with a 0x1 or 0x4 byte – followed by a URL – the file will be downloaded and executed. If the file is not properly downloaded or executed, the binary deletes itself from the host. This ability allows the hacker to update both the initial malware code executed to point toward new C2 servers and to install completely different malicious software as needed.
How to Protect against PoS malware like PoSeidon
Merchants should, by now, have all of their PoS and support systems behind a properly configured firewall, with logs and alerts enabled to the extent possible for both ingress and egress traffic. A review of firewall logs for the domains and IPs mentioned above could enable location and isolation of compromised systems by PoSeidon. Proper firewall techniques would also minimize network infiltration for this specific malware variant. Adding in the logging of DNS look-ups to the hard-coded domains identified is strongly recommended.
Merchants also could benefit from disallowing all remote access to their PoS networks, controlling access within their local networked environments, and ensure that their software is up to date with the most current patches in place. In this particular case, the exfiltration happens through port 80 which is generally used to access websites. Merchants should have their firewalls locked down to only allow traffic to known support sites on very specific ports and disallowing all other port 80 traffic for this part of their network.
Point-of-sale malware has proven to be a lucrative business for malware developers across the globe. The slow pace at which merchants in the USA are transitioning to chip and PIN technology only encourages malicious actors to evolve their malware. As more American merchants implement chip and PIN for credit card transactions it will be interesting to see how the malware developers adapt.
As with all malware identified and reported on, simply blogging about the malware doesn’t make it go away. It takes responsible IT and security staffs to actively maintain and protect their systems and networks. Level 3 Threat Research Labs blocked access to the active C2 and exfiltration servers over its network and will monitor changes to the domains in an effort to minimize the impact this botnet will have on the Internet.
![]()